- Command Post
- Posts
- Dispatch #022 | The John Hammond Approach
Dispatch #022 | The John Hammond Approach
How One Weak Link Can Bring Down Your Digital Park

7 Min Read
“Spared no expense.”
"Ah ah ah, you didn’t say the magic word.”
A few days ago, Jazmin and I bought new software to help us scale out our educational curriculum.
A clean, lightweight platform for running our webinar series without needing a 43-tab tech stack or a third-party integrator.
Click, swipe, purchased. Another tool in the belt and so we set the hour long onboarding call.
That’s when things got interesting.
Our onboarding session was led by someone from overseas. A friendly, polite offshore VA.
She was clearly trained to run through a checklist with military efficiency:
“Click here.”
“Now go here.”
“Check this box.”
“Boom, you’re live.”
We weren’t mad at the speed. We live in speed. But then came the curveball.
“Can I request remote access to your computer so I can help you move faster through the setup?” she asked with a smile on her face.
Negative. We don’t hand over our keys. Not to strangers. Not to vendors.
But it didn’t stop there.
“I’ll also need you to create a new user inside your agency account and give it full Agency Admin access.”
Absolutely not. Especially not when that user is titled something as vague and opaque as ‘Support’.
No face. No name. No country of origin. Just some shadow credential floating around in your system with nuclear launch codes access.
This is how small businesses get wrecked.
This is how your automations get bricked, your data gets siphoned, your reputation gets lit on fire and you’re left asking, “How did this happen?”
Here’s how. Too many companies are still operating on hope-as-a-strategy when it comes to Operational Security (OpSec)
And next week you’re crying in a ticket thread because your DNS records are scrambled and your Stripe account is frozen all because some “Support” user.
It happens every day and the worst part, the red flags were there the whole time.
You just handed them admin access and said, “We spared no expense.”
“The only thing more dangerous than a lack of information is the illusion of security.”
TL;DR | Quick Brief Links

Mission Debrief: Marketing Fixes All Our Problems
A local family-owned business who came to us through a personal referral.
They were heading into their slow season and wanted to pivot and focus on boosting their e-commerce presence and online sales.
They believed the answer was marketing.
They didn’t have a marketing problem. They had a manual process problem.
No documented systems. No automation. No streamlined operations.
Packaging? Manual. Shipping? Manual. Invoicing? Manual. Customer service? You guessed it, manual.
If we had flipped the switch on ads and driven traffic to their site, it would’ve collapsed under its own weight.
It would’ve been a Jurassic-sized disaster.
This wasn’t a business ready to scale, it was a business still being held together with tape, hand-labels, and long nights primarily falling on the shoulders of a single main Operator.
All they needed was one good marketing campaign to expose their biggest weakness.
The lesson?
It doesn’t matter how good your product is if your backend is built on blind trust and no protocols or documentation.
✅ What We Did:
Hit pause on all marketing conversations until the operational workflow was documented.
Helped the client identify which manual tasks could be automated immediately using existing systems.
Outlined a fulfillment infrastructure that could actually support demand before creating demand.
🔥 Tactical Takeaways (For Business Owners Seeking Service Providers)
Don’t build traffic funnels until your fulfillment engine can handle the heat.
Marketing doesn't fix operational chaos, it exposes it.
Access control isn’t paranoia, it’s protocol. Shared logins and mystery users are security threats, not convenience hacks.
If you’re handing out full admin access to people you’ve never met, you’re not building a business, you’re building a digital time bomb.

Let’s zoom out.
That onboarding session we had? It wasn’t a fluke.
That request for remote access? That anonymous support login? That happens every day inside small businesses across the country.
It’s death by convenience. Death by default settings. Death by “I didn’t think it mattered.”
And it’s exactly how you end up with a Dennis Nedry situation inside your operation.
In Jurassic Park, Nedry wasn’t the dinosaur. He wasn’t the hurricane. He was the IT guy.
He was the guy who got unrestricted access. The guy who got frustrated. The guy who exploited a lazy system.
And for a small business today? Your version of Nedry might be:
A former employee who still has login access.
A third-party contractor who was never off-boarded.
A shared account that multiple people use with no audit trail.
A tool you integrated that still holds sensitive API keys.
“You’re not going to get hacked by North Korea. You’re going to get wrecked by your own bad protocols.”
But here’s the good news. You don’t need an enterprise budget or a CISO to put real Operational Security into place.
You just need to follow 5 Simple Zero Trust Rules for Small Business:
Rule #1: Never trust. Always verify.
No one and we mean no one should get access without context, credentials, and purpose. If they can’t tell you why they need access, they don’t need access.
Rule #2: Create unique logins for every user.
No more shared logins. Every employee, contractor, or partner gets their own credential. That way you know who did what and you can shut access down without nuking the system.
Rule #3: Least privilege access
Only grant the minimum level of access required to do the job. Your designer doesn’t need access to Stripe. Keep the circles tight.
Rule #4: Revoke access immediately when someone leaves.
Even if it’s on good terms. Exit = Exit.
Build an off-boarding checklist.
Remove logins, API keys, calendar access, everything.
Rule #5: Know who’s inside the wire.
Conduct a quarterly access review. Audit your users. Identify ghost accounts. If you don’t recognize a name or a login, disable it. Immediately.
The obvious nature of these five rules is also their greatest downfall.
Because they are what most people see as “common sense” for exercising proper cyber hygiene, they are oftentimes overlooked.
This isn’t about fear. It’s about control.
It’s about protecting the digital infrastructure that powers your business.
It’s about operating like you’re already successful and successful businesses don’t leave the doors unlocked.
So before you roll out new software or before you add another tool, another team member, another task, take a moment and ask yourself.
- Do I know exactly who has access to what?
- And would I know today if someone went rogue?
Because once the raptors are out, it’s already too late to check the fence.

Time for your recon drop.
This is Actionable Intelligence that matters, globally and inside the HighLevel war room.

Perplexity Launches “Privacy Snapshot” in Comet Browser
The browser wars aren’t just about AI features anymore. They’re about trust, transparency, and total user control.
This week, Perplexity dropped a major privacy-focused update to their AI-powered browser, Comet.
This update signals a sharp turn in how AI tools handle data at the edge.
Comet now includes a “Privacy Snapshot” widget, giving users real-time visibility into their privacy settings directly from the homepage.
No more digging through menus or fine print. One click shows:
What’s being blocked
What your assistant can access
Where your data goes and where it doesn’t
They also overhauled the Comet Assistant settings to give users precision control over:
Which websites the assistant can interact with
When it can read tabs or history
How long data is stored (with personal queries deleted after 30 days)
Even more tactical: Comet uses a hybrid compute model.
Passwords and payment data? Stored locally, not in the cloud.
Assistant queries? Sent with minimal context, only when needed to complete a task.
Tracker and ad blocking? Enabled by default and no extensions required.
Why it matters:
This isn’t just a feature update, it’s a blueprint for Zero-Trust Architecture applied at the browser level.
Perplexity is proving that privacy-first AI isn’t just possible, it’s productized. This also puts pressure on other AI-native platforms to match the standard.
Tactical Implications:
AI assistants will increasingly sit between you and your customers. The question becomes, “Who owns that interaction and what data are they capturing?”
OpSec isn’t optional. If your internal tools don’t give you this level of control, your attack surface is already too big.
Expect privacy-first features to become a competitive edge. Tools that make security visible will outperform tools that bury it behind terms of service.
The modern web is conversational. The modern stack is assistant-powered.
The modern business needs to be built on protocols, not hope.
Resource: Introducing Privacy Snapshot

Here are my top three choices from this week’s feature drop.
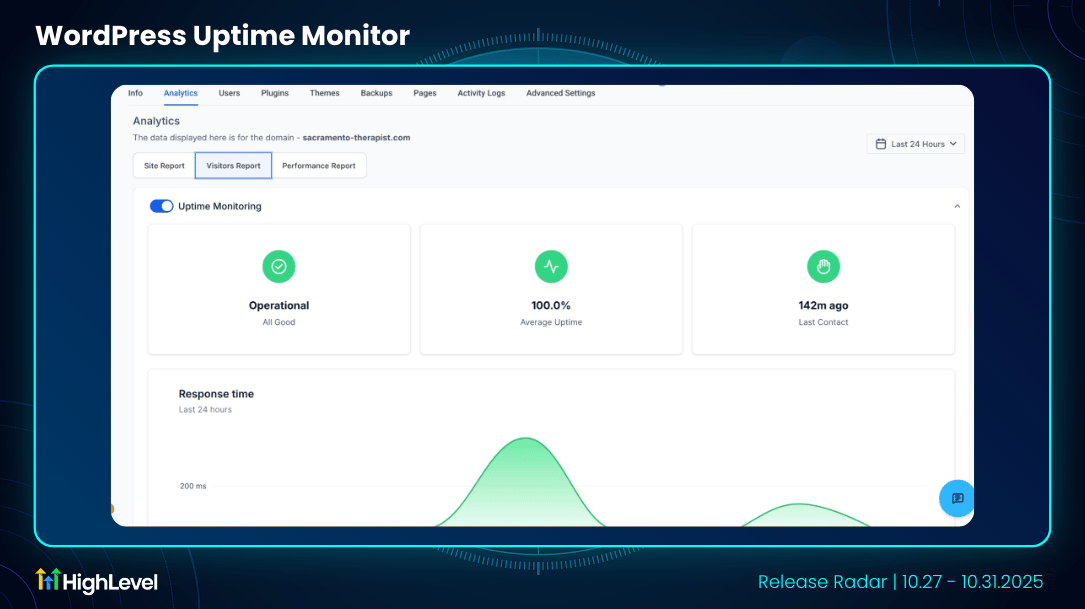
WordPress Uptime Monitor
With real-time availability checks, instant performance analytics, and insightful event tracking, you can maintain service reliability and respond quickly to potential disruptions all from within your WordPress hosting dashboard.
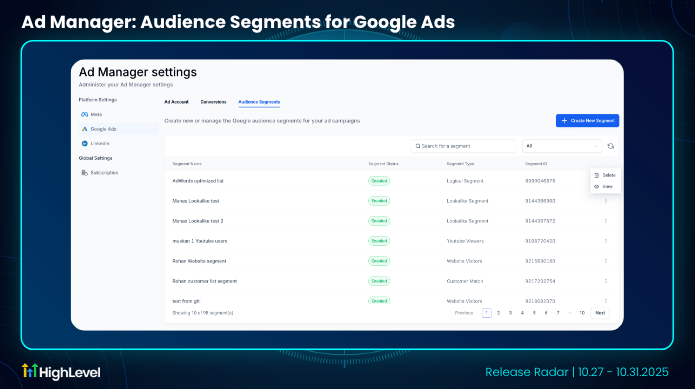
Ad Manager: Audience Segments for Google Ads
Enables users to create, manage and target audiences directly within the platform.
This release introduces end-to-end audience management; from segment creation in ad manager settings to seamless integration within campaign builder, ensuring better reach, personalization and campaign performance.
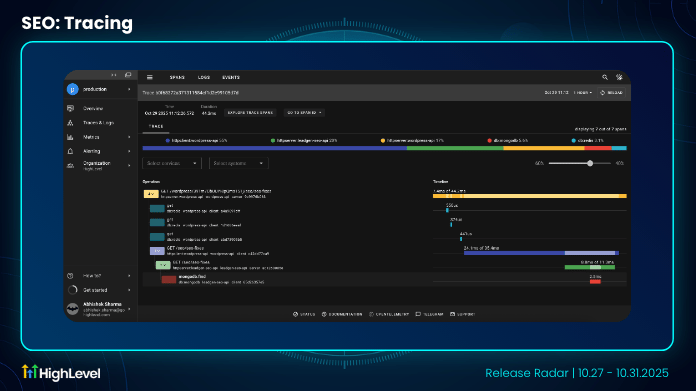
SEO Tracing
This enhancement allows developers to analyze MongoDB query execution times and overall API responsiveness.
With the integration of Uptrace, developers can now easily visualize traces for specific endpoints and understand their nested operations, helping identify performance bottlenecks and optimize query efficiency.
📺 Want the Full Feature Breakdown? Watch the full video below 👇️ 👇️👇️
🤑 Bonus Gift : View Google Presentation Slide Deck HERE.
Upcoming HighLevel Events
No upcoming live in person events have been listed yet.
However, there are several virtual events and town hall meetings scheduled.
Check out the line up below.

Alright Be Honest, How’d I Do?
Your opinion matters to me.
Seriously. I don’t write this newsletter because I’ve got nothing better to do.
I do it because I am hell bent on building REAL value for you.
Did this Dispatch deliver? Or should I call in an airstrike and start fresh?
Drop a comment or leave some stars
⭐️ ⭐️ ⭐️ Mission Accomplished – Tactical, tight, and ready for deployment
⭐️ ⭐️ Needs Reinforcements – Some hits, but it’s limping
⭐️ Mission Failure – Absolute FUBAR
Until next week,
Stay Frosty!
Michael

Reply